This axis aims to identify and solve frontier research topics in quantum cryptography, from two main perspectives. First by exploring the interplay between security models - including computational ones - and theoretical quantum cryptography. Second by unveiling fundamental and practical connections between quantum cryptography and hardware security.
Quantum-computational hybrid cryptography
We proposed a novel security model for quantum cryptography that we coined as the Quantum Computational Timelock (QCT) security model. It consists, as depicted in the figure below, in assuming that computationally secure encryption may only be broken after time much longer than the coherence time of quantum memories available at the time of protocol execution.
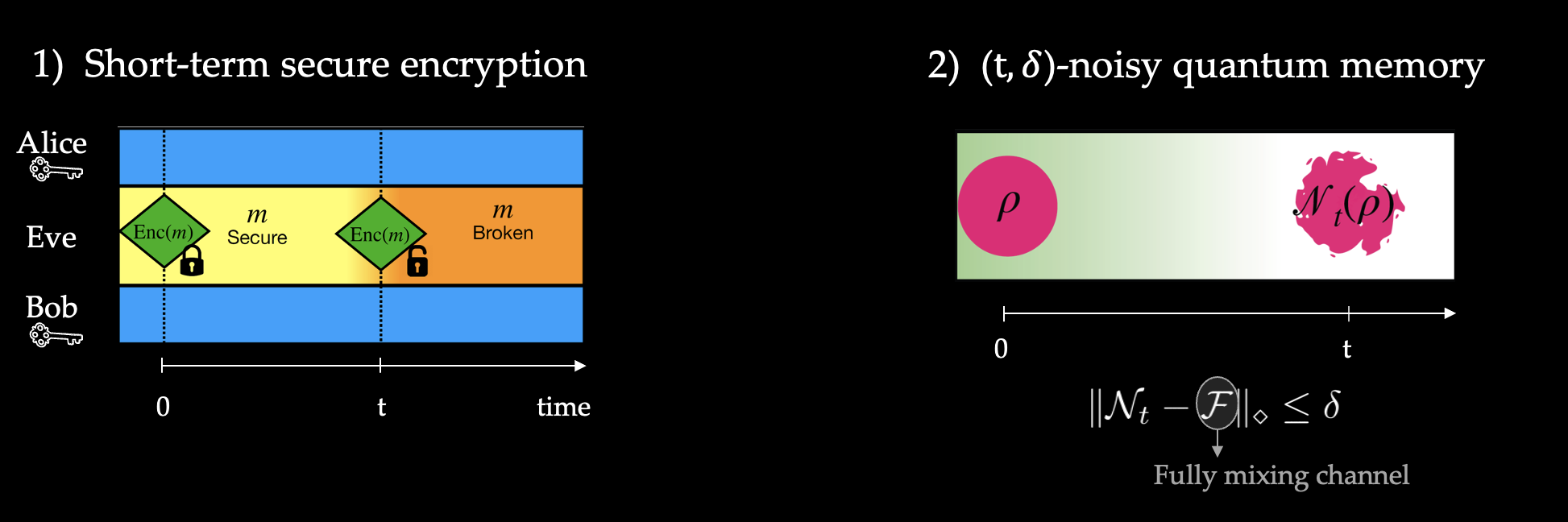
The QCT security model opens the possibility to propose new quantum cryptographic constructions and in particular to make use of encoding and security proof techniques that strongly depart from conjugate coding and have the potential to outperform traditional quantum cryptography, while offering everlasting security, that cannot be achieved with classical cryptographic protocols. We also intend to revisit and extend the validity of leakage-resilient cryptographic constructions, by grounding them on quantum-computational constructions.
We recently proposed [VA20] a key distribution protocol in the QCT security model whose security proof can be established by a reduction to a quantum to classical randomness extractor, and are currently working on proving security reduction with communication complexity problems (with Francesco Mazzoncini), and on connections with quantum pseudo-randomness (with Tristan Nemoz).
Researchers: Romain Alléaume, Peter Brown
Students: Francesco Mazzoncini, Tristan Nemoz
Device-independent cryptography and security proofs
Device-independent cryptography is concerned with the execution of cryptographic tasks with minimal assumptions. For example, by leveraging the intrinsic randomness present in Bell-nonlocality it is possible to produce certifiable randomness and secret key without trusting the quantum devices used within the protocol.

Whilst device-independent protocols afford us much stronger security guarantees this currently comes at the cost of significantly reduced ease of implementation, with low noise tolerances typically resulting in lower rates than more conventional quantum cryptography protocols. Nevertheless, it is possible to bridge the gap between theory and experiment by designing new protocols with improved tolerances, exploiting new mathematical tools designed to analyze these protocols. As a complementary line of research we are also investigating semi-device-independent protocols as a near-term high-security alternative to device-independence.
Along the lines of improved practicality we also aim to develop new security proof techniques with optimal finite-size effects by applying our expertise in convex optimization and entropies. Our work here will also apply beyond the setting of device-independence to more standard quantum cryptography protocols leading to improved performances across a wide spectrum of protocols. These security proofs
Researchers: Peter Brown, Thomas Van Himbeeck
Real-World Quantum Cryptography
Quantum Cryptography(QC) needs to overcome several challenges in order to become widely used in real-world applications. We identify in particular two main challenges: 1) Cryptographic Advantage, namely the capacity of using QC to obtain a competitive edge over existing cryptographic techniques; 2) Security evaluation and certification of quantum cryptographic implementations. Both challenges are at the heart of the EuroQCI initiative that aims to deploy a quantum communication infrastructure in Europe over the coming decade. We actively contribute to this large program through the projects ParisRegion QCI, FranceQCI and the CSA action PETRUS.
Regarding cryptographic advantage, our conviction is that one should not aim at constructions where quantum cryptography would just functionally replace classical cryptography, but on the other hand to design protocols where the use of QC combined with post-quantum cryptography (PQC) can present strict security gain over PQC alone.
As for certification, we take part of the international effort at ETSI QKD ISG and we have recently shown [KMQA21] how to conduct QKD vulnerability assessment in practice, based on a sound methodology inherited from Common Criteria. In future years, we intend to tackle this question from different angles, including QKD system engineering and the standardization of security model and proofs.
Researchers: Romain Alléaume, Thomas Van Himbeeck
Students: Francesco Mazzoncini, Tristan Nemoz